
The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
1
Metamora State Bank
Customer Education for Fraud:
Web, Phone, & Mobile

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
2
Metamora State Bank
Table of Contents
COMBAT SCAMS AND FRAUD ..................................................................................... 4
Protect your identity and accounts ................................................................... 4
APPROVED MSB METHODS OF CONTACT .................................................................... 5
Website ............................................................................................................ 5
Text ................................................................................................................... 5
Automated Calls ................................................................................................ 5
Email ................................................................................................................. 6
Online Banking Email ........................................................................................ 6
Direct Human Call ............................................................................................. 9
BUSINESS CUSTOMER EDUCATION ............................................................................. 10
Security Guidance ............................................................................................. 10
What is Dual Authorization? ............................................................................. 10
BEWARE OF PHISHING EMAILS ................................................................................... 11
What is Phishing? .............................................................................................. 11
10 Tips to Prevent Phishing Attacks................................................................... 11
BEWARE OF SMISHING TEXTS ..................................................................................... 13
What is SMiShing? ............................................................................................ 13
Recognize a SMiShing Attempt ......................................................................... 13
What to Do? Tips to Prevent Becoming a Victim ............................................... 14
SECURE YOUR WINDOWS DEVICES ............................................................................. 15
How to Turn on Windows Automatic Update for Windows 7: ........................... 15
How to Turn on Windows Automatic Update for Windows 10: ......................... 16
How to Turn on Microsoft Security Essentials (Anti-virus) ................................. 17
How to Turn on Windows Defender for Windows 10 ........................................ 18
Windows Firewall – Turn It On .......................................................................... 20
Backup Your Device .......................................................................................... 21

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
3
Metamora State Bank
Home Router .................................................................................................... 21
More from Microsoft ........................................................................................ 21
Additional Resource .......................................................................................... 21
SECURE YOUR ANDROID DEVICE ................................................................................. 22
SECURE YOUR IOS DEVICE ........................................................................................... 24
MOBILE APP DOWNLOADS ......................................................................................... 26
Android ............................................................................................................. 26
ITunes ............................................................................................................... 27
ONLINE BANKING INFORMATION ............................................................................... 28
Overview of Security and Enrollment ................................................................ 28
Security Data .................................................................................................... 28
Security Challenge............................................................................................. 28
BILL PAY IN ONLINE BANKING ..................................................................................... 29
What are the risks of using bill pay? .................................................................. 29
Ways to protect yourself ................................................................................... 29
SELF-ENROLLMENT PROCESS ...................................................................................... 30
STEP 1: ENROLLMENT ................................................................................................. 30
STEP 2: VERIFICATION ................................................................................................. 31
STEP 3: USERNAME & SECURITY CODE ........................................................................ 32
STEP 4: LOGIN ............................................................................................................. 33
STEP 5: USE LINK TO LOGIN ......................................................................................... 34
STEP 6: ENTER SECURITY CODE ................................................................................... 34
STEP 6: ENTER SECURITY CODE ................................................................................... 35
STEP 7: CHOOSE SECURITY QUESTIONS ....................................................................... 36
STEP 8: CREATE PERSONAL GREETING AND CHOOSE IMAGE ....................................... 37
STEP 9: LOGIN ............................................................................................................. 38
STEP 10: CONFIRM IMAGE AND PHRASE, ENTER PASSWORD ...................................... 39
STEP 10: CONFIRM EMAIL ADDRESS AND BEGIN ......................................................... 39

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
4
Metamora State Bank
Combat Scams and Fraud
Protect your identity and accounts
Do not click suspicious links or open unexpected attachments or texts. Be aware of Phishing emails and
Smishing texts.
Do not provide account info to links in emails or texts.
Do not provide account information over the phone to live or automated systems other than MSB Touch
Telebanc at:
o Toll Free – 877.MY MSB 411 or 696.7241
Always verify the identity of the person on the phone by calling back a known number, which are listed
below. Go to phone numbers.
Do not use unknown or unsafe devices to access your account.
o This includes cell phones, tablets or computers.
Use only phones, tablets and computers with the latest software and security patches.
o Use auto-update for all programs to receive the latest security patches. See Securing Your Device.
o Windows XP and Windows Vista (as of 4/11/2017) are no longer updated by Microsoft. Consider
upgrading to Windows 10.
https://www.microsoft.com/en-us/windows/windows-10-
specifications?OCID=win10_null_vanity_win10specs
o Use anti-virus software and keep it updated. See Securing Your Device.
o Keep your browser updated. See Securing Your Device.
o We are providing these instructions as a courtesy only. We cannot and will not provide any
support beyond providing these written instructions. Do not call for technical support.
Even with these recommendations, you, the consumer, must remain vigilant and suspicious of requests
for information in order to protect yourself. Be very careful and report all suspicious activity to MSB
immediately.
Report fraud immediately. Call us at 419.885.1996.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
5
Metamora State Bank
Approved MSB Methods of Contact
Website
Main website: https://www.metamorabank.com/
For support call your local branch
Text
MSB will never text you directly.
Automated Calls
MSB will never ask you to enter or give account information to an automated phone system outside of
telephone banking or debit card fraud calls.
You should always be suspicious of requests for personal banking information.
Debit Card Calls
MSB has automated calling related to debit card transactions.
o The calls originate from a 219 area code and will have live operators.
o What are those calls like?
Operator will identify as Metamora State Bank.
The operator will ask for the name on the card and or account number.
The operator may also ask for 2 of these items: Address, DOB and primary social
security number
They will describe the transaction for a card ending in XXXX to confirm that the customer
performed the suspicious transaction.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
6
Metamora State Bank
Email
Online Banking Email
MSB may email you from your online banking product, but the email will not include links to websites.
You may configure email alerts.
o When in doubt call us.
o The emails may include phone numbers to call which will most likely be an 800 number or a
published number.
o The email will never ask you to reply.
o The email will never have an attachment.
o The email will not include active links.
It may include an advisement to go to the website for information, but not a link.
o Email alerts about your accounts will usually come from[email protected]
o Online Banking Email Alert Configuration in figures below:

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
7
Metamora State Bank
Online Banking Alert Email Sample
From: myebanking@csiweb.com [mailto:myeba[email protected]] On Behalf Of no-reply@metamorabank.com
Sent: Thursday, May 03, 2018 10:01 AM
To: Jane Doe
Subject: The Metamora State Bank
As of today, your 'balance' alert on account 'Checking', ending in 111, has met the criteria you defined.
Criteria: Daily Balance Alert
Balance: $2,742.63
Available Balance: $2,732.63

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
8
Metamora State Bank
eStatement Email
You must opt-in to receive eStatement notices. Once enrolled you will receive eStatement availability
notices by email.
o The email will come from [email protected] [mailto:[email protected]] On Behalf Of
eStatement Sample Notice
From: [email protected]om [mailto:notify@csiweb.com] On Behalf Of statements@metamorabank.com
Sent: Saturday, April 14, 2018 5:08 AM
To: Jane Doe
Subject: Online Statement Message
Regarding Account xxxxxxxxx990
Dear Jane J Doe,
Your bank statement is available online.
You enrolled to receive online statements for your account. If you no longer wish to receive online statements, please
contact the bank.
Mortgage Application Email
If you filled out a mortgage application with us, you will possibly receive an email from one of our loan
officers.
o The email from address will look like this [email protected] and be sent to the email you
provided in your application.
o You can find our loan officers and their contact information here
https://www.metamorabank.com/about-msb/bank-officers/
o When in doubt call us. Phone Numbers

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
9
Metamora State Bank
Direct Human Call
MSB may call you individually from approved numbers, but if you were not expecting the call, you
should always call back a known number, which is listed below.
Calls from MSB will originate from these numbers, and you should call these numbers to verify identity or
suspicious activity.
o Metamora: 419.644.2361
Caller ID should show Metamora Bank depending on the number of characters allowed
o Sylvania:
419.885.1996, 419.882.3001, 419.882.4401, 419.882.4553, 419.882.4857
Multiple Lines call out. Caller ID should show Metamora State Bank or Metamora Bank
depending on the number of characters allowed
o You may receive calls from MSB about debit card fraud.
That number is will start with 219.
o If you filled out a mortgage application, you may receive a call from a loan officer from a number listed
above.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
10
Metamora State Bank
Business Customer Education
Security Guidance
Business Online has enhanced electronic transaction capabilities. It is extremely important that you heed all the
guidance in this document. Businesses should also consider additional security measures.
Business Security Measures
Use a Hardware firewall to protect your business network.
o Block unnecessary traffic, services, and websites.
Use Windows domain security features.
o User accounts
o Passwords with complexity requirements, expiration, attempt limits.
Limit employee access to only what is necessary.
Patch, Patch, Patch all devices.
Consider purchasing commercial grade antivirus and keep it updated.
Scan your network internally and externally for vulnerabilities regularly and remediate the vulnerabilities.
Back up and encrypt your important data regularly.
Use encryption when transmitting data.
Encrypt mobile devices.
Limit the use of removable storage.
Train and educate yourself and your staff.
o Phishing
o Smishing
o Securing Devices
What is Dual Authorization?
Dual Authorization is an important control in which a business can require two authorized employees to
complete separate actions in order for an electronic transaction to be completed. This provides protection
against insider malicious activity or from one compromised machine or user account. If your business can support
this control, we recommend using it for any relevant software you use.
What else can you do?
Keep your transaction limits as low as possible.
Monitor accounts and transactions regularly and carefully.
Use complex passwords, protect passwords for Business Online, and change them frequently.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
11
Metamora State Bank
Beware of Phishing Emails
What is Phishing?
Phishing is a form of fraud in which the attacker tries to learn information such as login credentials or account
information by masquerading as a reputable entity or person in email, IM or other communication channels.
Typically, a victim receives a message that appears to have been sent by a known contact or organization. An
attachment or links in the message may install malware on the user’s device or direct them to a malicious
website set up to trick them into divulging personal and financial information, such as passwords, account IDs or
credit card details.
Phishing is popular with cybercriminals, as it is far easier to trick someone into clicking a malicious link in a
seemingly legitimate email than trying to break through a computer’s defenses. Phishing campaigns often focus
on the year's major events, holidays and anniversaries, or take advantage of breaking news stories, both true and
fictitious.
To make phishing messages look like they are genuinely from a well-known company, they include logos and
other identifying information taken directly from that company’s website. The malicious links within the body of
the message are designed to make it appear that they go to the spoofed organization. The use of subdomains
and misspelled URLs (typo squatting) are common tricks, as is homograph spoofing -- URLs created using
different logical characters to read exactly like a trusted domain. Some phishing scams use JavaScript to place a
picture of a legitimate URL over a browser’s address bar. The URL revealed by hovering over an embedded link
can also be changed by using JavaScript. From TechTarget
10 Tips to Prevent Phishing Attacks
1: Learn to Identify Suspected Phishing Emails
These qualities can indicate an attack through an email:
It could duplicate the image of a real company.
The email may copy the name of a company or an actual employee of the company.
It might include sites that are visually similar to a real business.
It may promote gifts, or the loss of an existing account.
2: Check the Source of Information from Incoming Mail
Your bank will never ask you to send your passwords or personal information by mail. Never respond to these
questions, and if you have the slightest doubt, call your bank directly for clarification.
3: Never Go to Your Bank’s Website by Clicking on Links Included in Emails
Do not click on hyperlinks or links attached in the email, as it might direct you to a fraudulent website.
Type in the URL directly into your browser or use bookmarks / favorites if you want to go faster.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
12
Metamora State Bank
4: Enhance the Security of Your Computer
Common sense and good judgement are as vital as keeping your computer protected with a good antivirus to
block this type of attack. In addition, you should always have the most recent update on your operating system
and web browsers. See Below.
5: Enter Your Sensitive Data in Secure Websites Only
In order for a site to be ‘safe’, it must begin with ‘https://’ and your browser should show an icon of a closed lock.
6: Periodically Check Your Accounts
It never hurts to check your bank accounts periodically to be aware of any irregularities in your online
transactions.
7: Phishing Does Not Only Pertain to Online Banking
Most phishing attacks are against banks, but attacks can use any popular website to steal personal data such as
eBay, Facebook, PayPal, etc.
8: Phishing Knows All Languages
Phishing knows no boundaries, and can reach you in any language. In general, they are poorly written or
translated, so this may be another indicator that something is wrong. If you never go to the Spanish website of
your bank, why should your statements now be in this language?
9: Have the Slightest Doubt? Do Not Risk It
The best way to prevent phishing is to consistently reject any email or news that asks you to provide confidential
data. Delete these emails and call your bank to clarify any doubts.
1-9 From PandaSecurity.com
10: Change Your Passwords Frequently and When in Doubt
Change your passwords regularly – at least 4 times a year. Change it more if you can stand it. If you suspect you
have been tricked by a phishing email, immediately change the password and notify your bank.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
13
Metamora State Bank
Beware of SMiShing Texts
What is SMiShing?
SmiShing or SMS phishing is about sending false, fake text messages, claiming the mobile user that they have won
a free product or need to enter information or correct an account mistake. Within the fake text message, there is
a fake URL link that would lure the individual into clicking the link or a fake phone number. After the user has
clicked the link, that is when the hacking starts. The phone number may be to a hacker waiting to steal your info
to use at an ATM.
They may request:
Credit card information
Account passwords
Account information
Other valuable information
Recognize a SMiShing Attempt
There are several indicators of an email or text message scam, including:
Generic greetings.
o Instead of using your name, many message scams begin with a general greeting, such as: "Dear
[Company Name] customer."
Incorrect account information.
o The message will attempt to scare you with a large account balance, a warning that someone has
recently updated your account or a prize or special offer that must be claimed quickly.
A false sense of urgency.
o The message will attempt to compel you to act by threatening that your account is in jeopardy if
you do not update your information as soon as possible, or with a short deadline to claim a prize
or special offer.
Fake links.
o Links may appear valid, but typically go to fraudulent websites. Always check where a link is going
before you click. On a computer, you can do this by hovering your mouse over the link (without
clicking it) and looking at the website address in your browser's status bar, which is usually in a
bottom corner of the screen. If it appears suspicious, do not click the link. Alternatively, go directly
to the company website from your browser, not through any links sent in messages.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
14
Metamora State Bank
What to Do? Tips to Prevent Becoming a Victim
1: Avoid clicking on any UNKNOWN messages with links. Furthermore, think about who sent you the message. Is
it a person that you know?
2: Do not reply to text messages that have asked you about any of your personal finances.
3: If you have received any messages concerning your business assets or the partnerships that you have with
them and/or the bank that is associate with them, call the business or businesses to see if it is a
legitimate request before responding.
4: Be on the lookout for messages that contain the number "5000" or any number that is not a phone number.
This is a strategy where scammers have masked their identity so their location and identity are not traceable.
5: If the text messages (along with the unknown number) urges for a quick reply then that is a clear sign of
SmiShing! Do not respond!
6: Do extensive research before replying to any message. There are plenty websites that allow anyone to run
search based on a phone number and see any relatable information about whether or not a number is legit.
7: Never call back a phone number that was associated with the text that concerns you.
8: If the message states, "Dear user, congratulations, you have won...." It is a clear sign for SmiShing.
9: Check the time when the unknown message was sent. If the text message was sent at an unusual time, then
that is another sign of SmiShing.
10: Make sure to be aware and informed of your bank apps policy. It is important to acknowledge there is a
policy that protects your money along with other personal information that is associated with the bank account.
11: Send the fraudulent message to the bank and wireless carrier.
12: Delete the fraudulent message.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
15
Metamora State Bank
Secure Your Windows Devices
This only provides instructions on Windows updates on Windows computers. Your computer will have other
programs that you need to set up for automatic updates such as Adobe, Java, and other browsers such as Google
Chrome or Mozilla. You will also need to investigate your tablet and phone to learn how to protect it.
*** We are providing these instructions as a courtesy only. We cannot and will not provide any support beyond
providing these written instructions. Do not call for technical support.
How to Turn on Windows Automatic Update for Windows 7:
http://windows.microsoft.com/en-us/windows/turn-automatic-updating-on-off#turn-automatic-updating-on-
off=windows-7
From Microsoft:
To have Windows install important updates as they become available, turn on automatic updating. Important
updates provide significant benefits, such as improved security and reliability. You can also set Windows to install
recommended updates automatically, which can address non-critical problems and help enhance your computing
experience. Optional updates and Microsoft updates are not downloaded or installed automatically.
For more information about automatic updating and installing Windows updates, see Understanding Windows
automatic updating and Install Windows updates in Windows 7.
To learn more about the types of updates that Microsoft publishes, go to the Microsoft updates
terminology article on the Microsoft Help and Support website.
1. Open Windows Update by clicking the Start button . In the search box, type Update, and then, in the list
of results, click Windows Update.
2. In the left pane, click Change settings.
3. Under Important updates, choose the option that you want.
4. Under Recommended updates, select the Give me recommended updates the same way I receive
important updates check box, and then click OK. If you are prompted for an administrator password or
confirmation, type the password or provide confirmation.
You can also choose if you want to allow anyone to install updates by selecting the Allow all users to install
updates on this computer check box. This applies only to updates and software that are installed manually;
automatic updates will be installed regardless of the user.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
16
Metamora State Bank
How to Turn on Windows Automatic Update for Windows 10:
https://support.microsoft.com/en-us/help/17154/windows-10-keep-your-pc-up-to-date
1. Select the Start button, then select Settings > Update & security > Windows Update, and then
select Change active hours.
2. Choose the start time and end time for active hours, and then select Save.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
17
Metamora State Bank
How to Turn on Microsoft Security Essentials (Anti-virus)
http://windows.microsoft.com/en-us/windows/getting-started-with-security-essentials
From Microsoft:
There is not much to do. Microsoft Security Essentials works in the background to protect your PC. It checks for
updates automatically a few times a day and does not slow your PC down while it works.
Simple color-coding, simple actions
You can keep track of how your PC is doing by looking at the Microsoft Security Essentials icon in the notification
area at the far right of the taskbar. Green means everything is okay, yellow means that your PC is potentially
unprotected, and red means that your computer is at risk.
When you see yellow or red, click the icon and you will be able to see the details and take actions. Usually the
best thing to do is to choose Clean computer so that the threat can be removed.
If you want to delete threats automatically whenever they are identified, open Microsoft Security Essentials, click
the Settings tab and then choose Default actions.
Scanning right now
Open Microsoft Security Essentials and you will be on the Home tab. You can select a Quick scan or a Full scan
(and then click Scan now).
The quick scan will look for viruses in all the places they are most likely to hide. It is a good choice when you are
just checking on the health of your PC.
However, if something makes you think your PC is infected with a virus or spyware, we recommend a full scan.
Your computer will be a little slower while it is running, but the full scan looks everywhere for possible problems.
Scheduling scans
By default, Microsoft Security Essentials runs a scan of your PC once a week when you are probably asleep (2:00
am on Sunday).
If you want to adjust this, open Microsoft Security Essentials and click the Settings tab. Under Scheduled scan,
you will be able to change the day and time as well as the type of scan.
Scanning more than just your hard drive
It may be useful to scan external drives and USB drives since they can be infected too.
Open Microsoft Security Essentials and click the Settings tab. Go to Advanced and click the option to Scan
removable drives. Whenever scans run, your removable drives will also be scanned (if they are attached to your
PC). If you want to run a scan right away, go back to the Home tab and click Scan now.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
18
Metamora State Bank
How to Turn on Windows Defender for Windows 10
To start Windows Defender, you have to open the Control panel and Windows Defender Settings and click on Turn
On, and ensure that the following are enabled and set to On position:
1. Real-time protection
2. Cloud-based protection.
When there is no security software protecting your computer, you will see notifications like these appear.
Clicking on it will show you the installed security apps on your system. If you miss this notification, you can see it
in the Notification & Action Center.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
19
Metamora State Bank
Clicking on it too will show you the installed security apps on your computer, as follows.
Select Windows Defender and then click on the Turn on button. Windows Defender will start. The first thing you
want to do when this happens, is to update your definitions.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
20
Metamora State Bank
Clicking on the Settings link in the top right corner will open the following panel. You can also access it
via Settings > Update & security > Windows Defender.
Once here, ensure that Real-time protection and Cloud-based protection is set to On. You may also set Automatic
sample submission to the On position. You may then configure Windows Defender according to your needs.
Windows Firewall – Turn It On
Always, always turn on Windows Firewall.
Windows 10
To turn Windows Firewall on or off, select the Start button, open Windows Defender Security Center > Firewall
& network protection, choose a network profile, and then under Windows Firewall, turn it on or off.
Windows 8 and 7
Open Windows Firewall by clicking the Start button , and then clicking Control Panel. In the search box,
type firewall, and then click Windows Firewall.
In the left pane, click Turn Windows Firewall on or off. If you are prompted for an administrator password or
confirmation, type the password or provide confirmation.
Click Turn on Windows Firewall under each network location that you want to help protect, and then click OK.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
21
Metamora State Bank
Backup Your Device
You need to plan ahead so that you can recover form attacks. Many attacks like ransomware ruin, corrupt, or lock
the data on your computer. You can combat that by regularly taking backups of your machine. Use an external
hard drive and/or a secure cloud service to perform your backups. Many of these solutions require very little
technical skill to use, but can save your important data.
Home Router
Take the time to understand your home router and use its firewall or security capabilities.
More from Microsoft
Please go to this page and read more tips guidance from Microsoft.
https://support.microsoft.com/en-us/help/17228/windows-protect-my-pc-from-viruses
https://support.microsoft.com/en-us/help/4013550/windows-protect-your-pc-from-ransomware
Additional Resource
https://staysafeonline.org/stay-safe-online/online-safety-basics/

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
22
Metamora State Bank
Secure Your Android Device
From TechRepublic http://www.techrepublic.com/blog/10-things/10-security-measures-you-should-take-with-your-android-device/
1: Do use strong passwords
...For everything mobile. Every. Single. Thing. From your lock screen to your email, to your app logins. No
password should be simple to remember or enter. You have heard this countless times, but it always, always,
always bears repeating. First, not having a lock screen password should not even be considered an option.
Second, never use a simple password for this first line of defense. Ever. Make this password (PIN or pattern) as
complicated as you can handle. The more complicated your password, the harder it will be for others to get to
your data.
2: Do use two-factor authentication on everything possible
Google, Facebook, and Amazon: They all offer two-factor authentication. Employing this on each service should
not be an option. When these accounts get hacked, bad things happen. You can lose money, you can lose friends,
and you can lose information. Two-factor authentication can go a long way toward preventing this from
happening—and it is not difficult to do. You will definitely want to make use of the Google
Authenticator or Authy to dole out the six-digit keys to get you into your accounts.
3: Do encrypt your device
Yes, your device performance will take a slight hit, but the added security is worth it. Once you have encrypted
the device, you will add an extra, required password (during boot) that cannot be circumvented. If you purchase
a newer Android device (one that shipped with Marshmallow), you are already enjoying full device encryption. To
find out if your device is encrypted, go to Settings | Security and look for the Encryption section. If it is listed as
Encrypted, you are good to go.
4: Do use a password manager
You should not allow any apps to save your password for you, unless the app is designed specifically for saving
passwords. The last thing you want to do is have all your passwords cached on your mobile device. If you lose it
(or it is stolen), all those passwords are there for the taking. Instead of saving the passwords, use a solid
password manager (like 1Password). Yes, this will be a bit of an inconvenience, but the added security will be well
worth it.
5: Don’t skip the updates
There is a reason why apps update, and it is not just for features. Apps update to fix security issues as well. If you
do not bother to update those apps, you may leave yourself open to security flaws that could lead to terrible,
horrible, no good, very bad... issues. You should always update your apps. The longer you wait, the longer your
device stands vulnerable.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
23
Metamora State Bank
6: Do lock your apps
There are apps in the Google Play Store that allow you to secure other apps with passwords. This means you can
choose which apps you want to password protect. Once protected, those apps can be opened only after entering
the required password. No password, no entry. One of the best apps for this purpose is AppLock. It is reliable,
easy to use, free, and does the job without adding so many bells and whistles as to complicate the process.
7: Do manage your app permissions
Thanks to Android Marshmallow, managing app permissions is finally in the hands of the end user. This means
you can remove permission for an app to say, access the device mic or camera. For example, you do not want
Facebook to be able to use your location. You can now disable that particular feature from the app. To do this, go
to Settings | Apps and then tap the gear icon and tap App Permissions. The system is straightforward and does a
great job of empowering the user. Just make sure you do not disable permissions for system apps (which are
hidden, by default, in the Permissions Manager window).
8: Don't use open Wi-Fi networks
If you are at a coffee shop and its wireless network is not password protected, do not use it—especially if you will
be transmitting sensitive information. If you find yourself faced with an open wireless situation, use your carrier
network instead. If you have no choice, use one of the many VPN services available (such as TunnelBear VPN).
When using an open network through a VPN connection your data will at least be encrypted and a bit more
challenging to steal.
9: Don't install apps from a third party
You may be tempted to install that really cool sounding Android app from a third party. Do not. You never know
whether that app might contain a dangerous piece of malware that could walk away with your sensitive
information. Limit yourself to only installing from the Google Play Store. Even then, read the reviews of the app in
question before installing. A few minutes of your time to check into an app (prior to installation) will be well
worth the effort.
10: Do add your device with the Device Manager
Google has this handy tool called the Android Device Manager. Once your device is added, you can track it if it is
lost—or even remotely wipe it, should you fear that your sensitive data could become compromised. To enable
this feature, go to Settings | Google | Security and then tap to switch on both Remotely Locate This Device and
Allow Remote Lock and Erase. You should do this immediately with your device. If you do not, and you lose your
device, the Device Manager will do you no good.
Bonus tip: Do use the guest account feature
When handing over your device to another user (for whatever reason), make use of the guest account feature. If
you pull down the notification shade (on Marshmallow, you must do this twice), you will see a small icon
representing your user account. Tap that icon and you can then add a guest user. Once added, when you hand
that device over, tap the user icon to switch to the guest account. Making use of this system means the guest
user cannot access your data (unless they know your security password/PIN/pattern).

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
24
Metamora State Bank
Secure Your iOS Device
From COMPUTERWORLD http://www.computerworld.com/article/3047179/apple-ios/14-privacy-and-security-settings-every-ios-user-should-use.html
1: Alphanumeric passcodes
You probably already use a 4-digit passcode, but you can improve that with a 6-digit or alphanumeric code. You
change this in Settings>Touch ID & Passcode, select Change Passcode and then tap the small Passcode Options
dialog you will encounter. Alphanumeric codes are the toughest to decipher, so use one. You should also do
yourself a favor and set up Touch ID or Face ID.
2: Erase data
At the bottom of the Settings>Touch or Face ID & Passcode screen you will find the Erase Data toggle. Set this to
green and all data on your iPhone will be erased after 10 failed passcode attempts.
3: Two-factor authentication
One of your most powerful protections, two-factor authentication means that when you enter your Apple ID and
password for the first time on a new device, Apple will ask you to verify your identity with a six-digit verification
code using one of your other devices. Manage this on your Apple ID account page.
4: Find My iPhone
Do not be a loser – enable Apple’s Find My iPhone (Settings>iCloud>Find My iPhone) on all your devices. You
should also enable Send Last Location in order that your iOS device will share the last place it was before battery
life expires.
5: Location protection
Your iPhone automatically gather your favorite locations. This can be useful, but you can turn this feature off in
Settings>Privacy>Location Services>System Services and then Frequent Locations, which you must turn off. You
can erase data that may already have been gathered by tapping the Clear History button. You can also control
which of Apple’s system services are tracking your location by looking at Settings>Privacy>Location
Services>System Services. Here you can review those Apple apps that use your data and disable the ones you do
not use, but do not disable Find My iPhone.
6: More location
Many apps request access to that data even when you are not using them. You can review what permissions you
have given to which apps in Settings>Privacy>Location Services, where you can assign location permission access
to each app. Limiting access to this data may limit what some apps can do, but the trade-off is privacy – you can
always change the setting when you want to use an app, but are you sure you wanted to share location data with
an app you used just once?
7: Who gets your data?
Many apps seem demand access to personal data such as email, contacts of calendar information. Do you know
why? Apps will ask for permission to use this information, but you can change and review how much access you
provide to third party apps in Settings>Privacy and select which apps you trust enough to use this data.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
25
Metamora State Bank
8: Hard payments
Is it really too time-consuming to manually approve every purchase you might make on your iPhone? Protect
yourself by choosing Always Require when a payment dialog appears.
9: Delete iMessages
Do you want your iMessages to be read by anyone who might break into your iPhone? No? Open
Settings>Messages and in the Keep Messages section set 30-days, the shortest period Apple allows.
10: Lock screen
Previews of messages, notifications and emails can appear on your lock screen, meaning anyone in possession of
your device can monitor these communications, even if they cannot get into your phone. Change this in
Settings>Notifications>Messages and Mail. Maximize privacy by disabling Show Previews so your
communications will not appear on the lock screen.
11: Passcode free?
You can leave Today, Notifications View, Siri, Reply with Message, Wallet visible and (to a point) accessible on
your lock screen, but you can disable this for each of these in Settings>Touch/Face ID & Passcode.
12: Safari privacy
Ads networks want your data. Not only do they want this to sell you stuff, but they also try to make dollars selling
demographic information about you to advertisers. Control what you share in Settings>Privacy>Advertising and
enable the Limit Ad Tracking toggle. You should then tap the Reset Advertising Identifier tool to anonymize
yourself. Moreover, avoid using Google services.
13: Use DuckDuckGo
Change your search engine to DuckDuckGo in Settings>Safari>Search Engine, because the search engine does not
collect information about you.
14: Auto-lock
Lower the auto-lock time to 30-seconds in Settings>General>Auto-Lock.
The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
26
Metamora State Bank
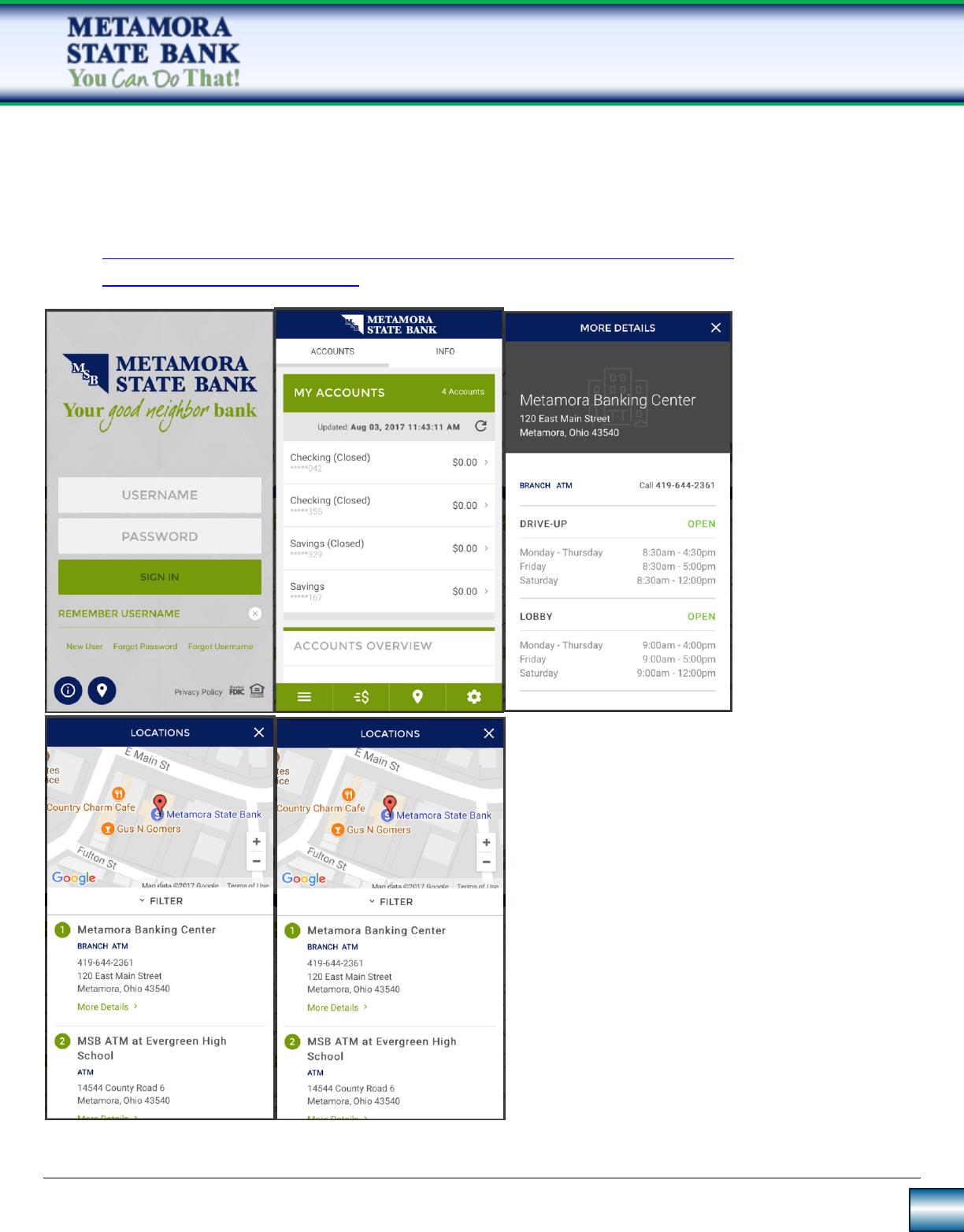
Mobile App Downloads
Android
https://play.google.com/store/apps/details?id=com.csiweb.digitalbanking.bk0457
For support call your local branch

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
27
Metamora State Bank
ITunes
https://itunes.apple.com/us/app/metamora-state-bank-for-iphone/id1069500760?mt=8
For support call your local branch

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
28
Metamora State Bank
Online Banking Information
Overview of Security and Enrollment
For the initial signup, the request goes to bank. Then bank contacts customers by phone, to confirm the
application. Then the bank grants access, and the customer completes the process on his or her own. The process
is the same for mobile.
Click here to view enrollment steps.
Customers can turn their debit card on and off. Customers can call about travel plans to make sure that debit
cards work.
The Internet Banking login process includes several layers of security. This security is intended to prevent
unauthorized access to your account, validate your identity, protect your account information from fraudulent
use, and prevent the theft of your identity.
For support call your local branch
Security Data
The following security information, which you set up during an initial login session, is used to protect your
Internet Banking sessions:
Username – setup by user
Authentication image – setup by user – verify it matches
Authentication pass phrase – setup by user – verify it matches
Password – setup by user
Email address –
Challenge questions – set up by user- on new computers
Computer registration – check a box remember this device
Mobile can have a password then you can set up a pin and a fingerprint
Security Challenge
A security challenge occurs when your financial institution's online banking software does not recognize the
computer from which you are attempting to log in. The purpose of the security challenge is to prevent
unauthorized people from accessing your account information.
The challenge requires you to prove your identity by correctly answering one or more of the challenge questions
you selected when you set up the authentication security data.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
29
Metamora State Bank
Bill Pay in Online Banking
This requires mobile and/or online banking.
Online banking requires you to use an email account.
o Protect access to this account at all times because it is used for communication from online
banking.
If you elect to use online banking, you can then register for bill pay.
Once you register for bill pay, payees can be established.
o Recipients receive the money in one of two ways depending on the recipient’s capability:
Paper check
These are cut and sent in advance of the scheduled day.
Electronic ACH
These funds are immediately transferred on the scheduled day.
For support call your local branch
What are the risks of using bill pay?
If you do not protect your computer or device in the manner described, a hacker could take over your
machine.
After taking over your machine, they could watch you login into online banking.
After learning your online banking credentials, they could add themselves as a payee in online banking
and pay money out of your account into theirs.
Ways to protect yourself
Log into your account regularly and check your balances, activities, and payees.
Secure your device as described previously.
Monitor your emails diligently for notifications of changes to your online account and payees.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
30
Metamora State Bank
Self-Enrollment Process
Step 1: Enrollment
The first screen the user will see in during the self-enrolment process will look like the following.
After completing the form, the user will be able to proceed. The application will NOT let the user proceed if they
meet one of the following exceptions.
- SSN already exist in Internet Banking
- SSN is tied to another Internet Banking profile
- SSN does not bank at the Financial Institution
- User is enrolling with Business TIN
- User has no Credit History (example: 17 year old is self-enrolling)

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
31
Metamora State Bank
Step 2: Verification
The customer must confirm details from their credit file to proceed.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
32
Metamora State Bank
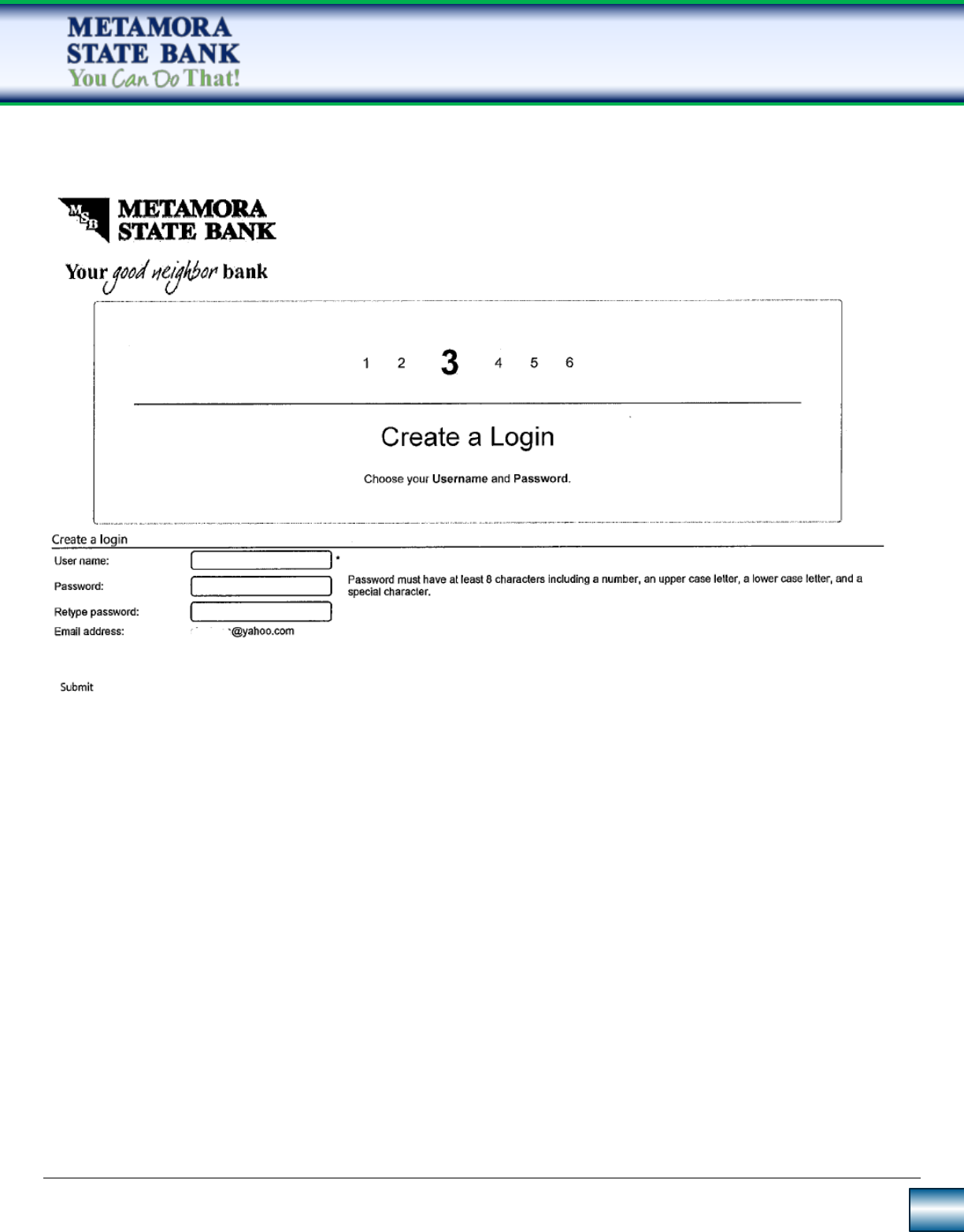
Step 3: Username & Security Code
Once verified the user will need to create a Username & a onetime Security Code.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
33
Metamora State Bank
Step 4: Login
The last page the user will see is the login screen. Like noted on the page, user will need to use the link provided
in the email they used during step 1.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
34
Metamora State Bank
Step 5: Use Link to Login
Click the link that comes to the registered email to login.
Step 6: Enter Security Code
Click the link that comes to the registered email to login.
The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
35
Metamora State Bank
Step 6: Enter Security Code
Choose a username and password.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
36
Metamora State Bank
Step 7: Choose Security Questions
Select questions and answers to be used for verification.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
37
Metamora State Bank
Step 8: Create Personal Greeting and Choose Image
Create a greeting and select an image to use for verification.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
38
Metamora State Bank
Step 9: Login
Here you can select to remember the device to cut down on the number of steps.

The information, format, content, processes, methods and descriptions contained in this document are intellectual property and is also proprietary and confidential to Metamora State Bank
and may not be used, disclosed, or duplicated conventionally or electronically for commercial purposes outside of official MSB bank business. Violation of this policy is a felony theft under state
law and is punishable in a court of law.
39
Metamora State Bank
Step 10: Confirm Image and Phrase, Enter Password
Step 10: Confirm Email Address and Begin
